Since the 2025 FISMA Audit for the VA’s 2024 Fiscal Year (FY) has not been released yet, I will be using data from both the 2023 FISMA Audit and the 2024 Financial Report.
We begin our journey with first understanding the NIST CSF Core Functions and Categories. The NIST’s Core Functions include:
- Govern
- Identify
- Protect
- Detect
- Respond
- Recover
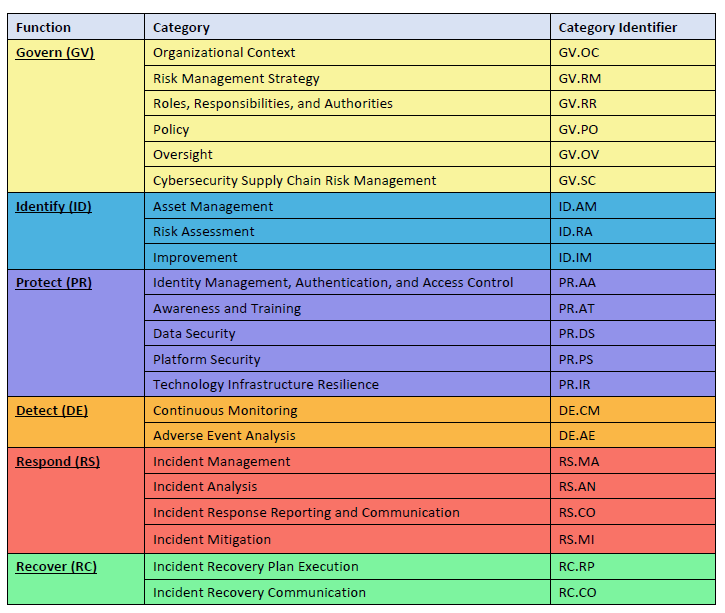
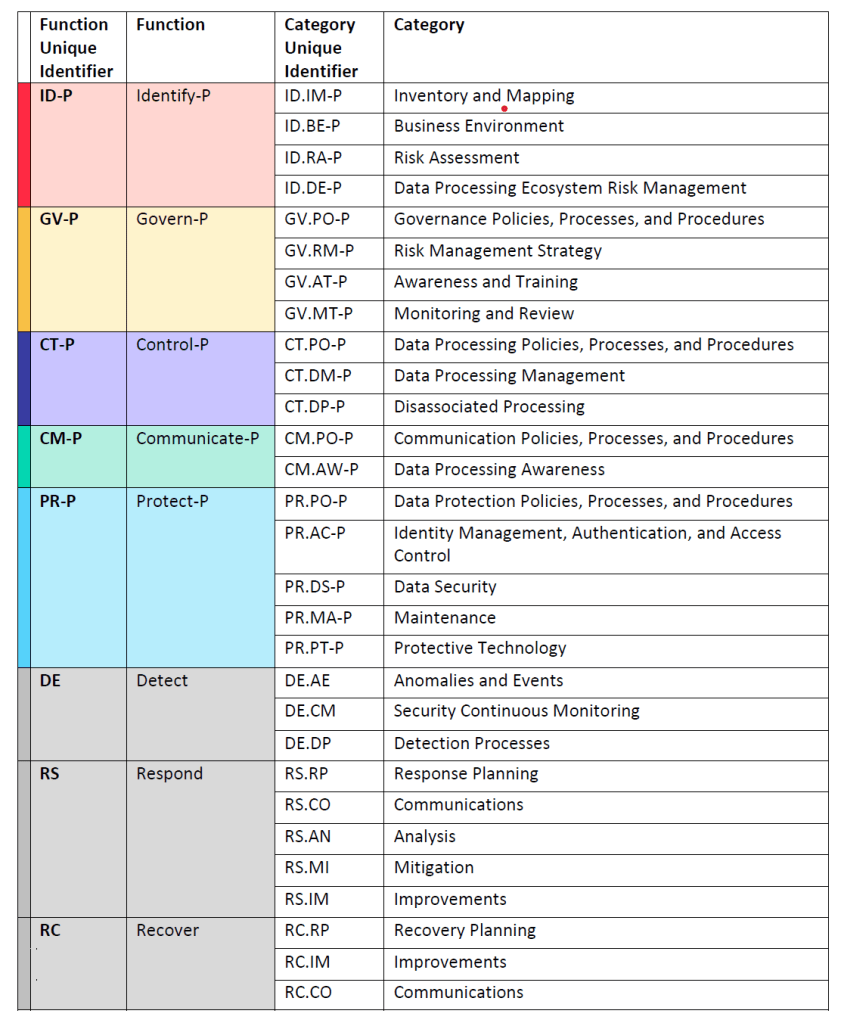
Each one of these Fuctions has several of their own Categories. And each one of the Categories has their own Subcategories (in the above photo listed under “Category Identifier”). In the “NIST CSF Summary” tab in his tool, Masserini refers to the Subcategories as Controls not because they are the same thing, but because Subcategories map to specific Controls.
- Subcategory: describes desired cybersecurity outcomes
- Control: specific security requirements or safeguards explaining how to achieve a cybersecurity outcome
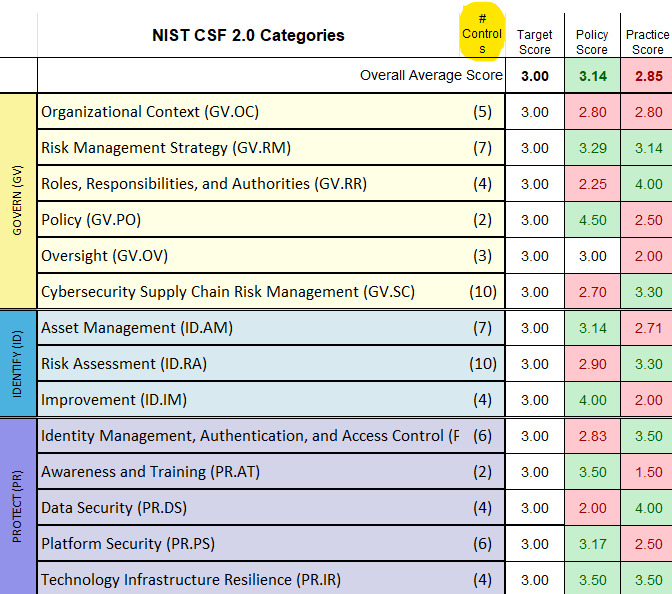
Now when you navigate over to the “CSF 2.0” tab in the tool you will see official documentation given by NIST. The NIST CSF 2.0 provides Implementation Examples and Informative References for each Subcategory. It is these Informative References that list our Controls. CSF 2.0 outcomes are broad. The Informative Reference documentation is specific and control-based. Therefore, the Informative References are essentially an answer on what actions to take in order to meet the intent of the outcome stated by the Subcategory.
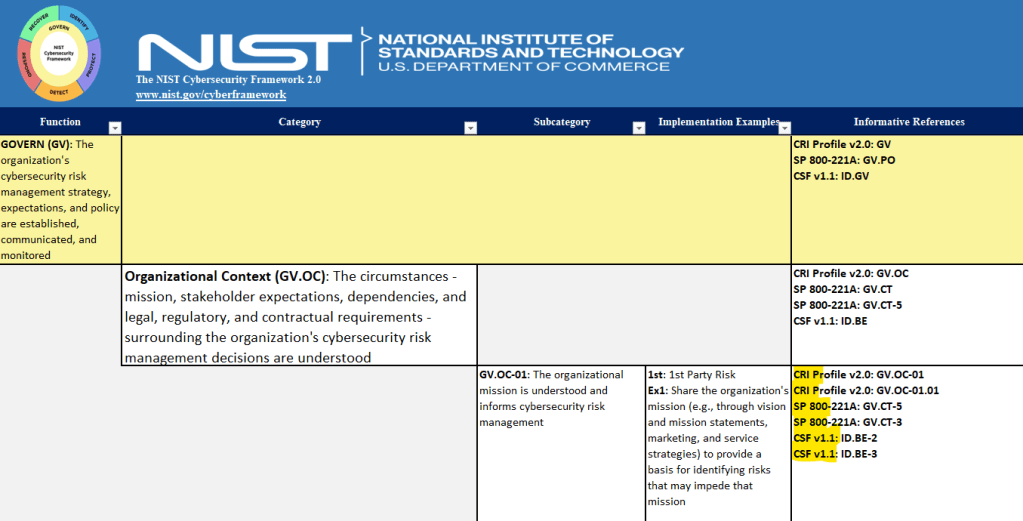
As I’m walking through Masserini’s Maturity Tool, there are a lot of terms and acronyms I am not familiar with yet. For example, these Informative References point to terms like “CRI Profile” and “SP 800”. So we also need to start defining key terms as we continue to dissect the tool:
- The Cyber Risk Institute (CRI) Profile v2.1 is based on NIST’s “Framework for Improving Critical Infrastructure Cybersecurity” and pulls from other cybersecurity frameworks and regulations (such as ISO, FFIEC, etc.) into a single profile. This risk management tool is mainly used by large financial institutions because they are able to cover all their bases (AKA regulatory requirements based on legal and voluntary standards) in one go. NIST CSF alone can be used for technology companies, government agencies, and SMBs (small-to-medium businesses). The CRI Profile heavily draws from NIST’s framework by including all of the same Functions, as well as an additional “Extend” Function. Therefore NIST CSF 2.0 Subcategories are easily able to translate to CRI’s Diagnostic Statements.

- NIST’s Special Publication (SP) 800 series is a foundational series of guidelines, recommendations, and technical documents that was developed to address the cybersecurity needs of U.S. Federal Government information systems. Therefore the SP 800-series is in accordance with FISMA’s statutory responsibilities.

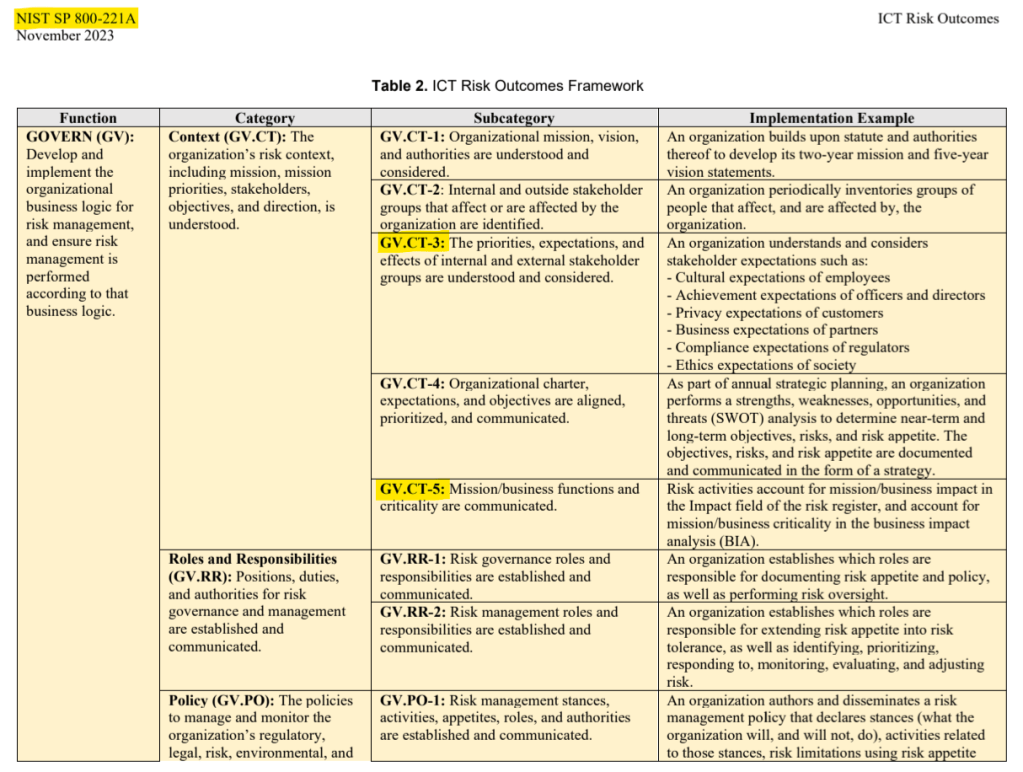
I’ve also seen scattered throughout several different documents the acronym “ERM.” Therefore I feel it is a highly relevant term that I’ll also need to define before continuing my use of the tool:
- Enterprise Risk Management (ERM) is a a structured, organization-wide approach to identifying, assessing, managing, and monitoring risks that could impact an organization’s objectives. Unlike traditional risk management, which often focuses on specific areas like finance or IT, ERM integrates risk management into all levels and functions of a business, including strategic planning and decision-making. ERM is not a reference to a framework, rather it is a type of methodology designed to address risk awareness and response. NIST frameworks align with ERM principles.
Next is the CIS Controls:
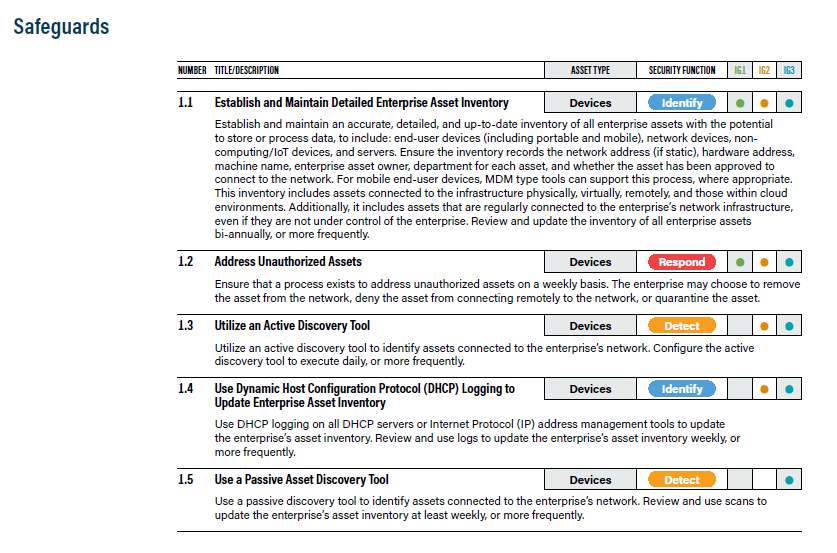
- CIS Controls v8.0 describes itself as an activity developed by an international community of volunteer institutions that allows organizations to map Controls to regulatory and compliance frameworks. It is one part of the CIS Security Best Practices (along with CIS Benchmarks) and has evolved from data-driven approaches like the Community Defense Model (CDM), Multi-State Information Sharing and Analysis Center (MS-ISAC), and the MITRE ATT&CK Framework. Unlike the controls that have come before, the CIS acitivities are prescriptive and highly focused. The CIS Controls map to various ERM frameworks such as NIST, FISMA, and ISO. There are 18 Controls listed in CIS 8.0 and they are categorized into subsets known as Implementation Groups (IGs). The IGs help companies apply the Controls that are associated with a similar risk profile to theirs. Each IG builds upon the one before it. Also, every Control has a number of Safeguards which are specific actions on how to implement the Control.

The last thing I’d like to address on Masserini’s “CSF 2.0” tab is under the Informative References there is documentation listed pointing to CSF v1.1. This thoroughly confused me at first. Was 2.0 not a complete document? Why would it be referencing a previous version? Shouldn’t they have included it when they updated the new version? Well yes, they did.
Unlike the other external controls and standards listed under the References, anything referring back to CSF v1.1 is simply listed there for legacy mapping. This way GRC analysts who were already using 1.1 at their organization could easily translate previous controls to the new framework. It is not an answer to an outcome. It is a reference to where the 2.0 outcome was listed in the 1.1 version.
NIST Privacy Framework
Very quickly I do want to glance over at the “Privacy Framework” tab. We won’t be spending too much time here because I’ve decided that I am going to deconstruct the VA’s FISMA and Financial Audit all the way through mapping it just to the CSF 2.0 before I do the same thing for the Privacy Framework.
However I did want to mention in this post that I wouldn’t have known to make that my strategy if I didn’t break down exactly what the Privacy Framework was. So here it is:
- NIST’s Privacy Framework exists because the cybersecurity framework is not sufficient enough on its own to cover data privacy concerns. Privacy risks can occur without a cybersecurity risk occurring. Just to give you an idea on how closely the CSF and Privacy Framework (PF) are related, you should know that the CSF 2.0 was published in February 2024 while PF 1.1 was just published over a year later in April 2025. They share many of the same Functions, however they have 2 new Functions (Control and Communicate) and also they’ve removed the Detect, Respond, and Recover Functions. The last 3 Functions are still included on the table because they do note organizations may choose to include these in order to further support the management of privacy risks.
In Part 3 I will show you what I’ve done so far in terms of how I’ve been extracting information from the FISMA Report and mapping it to NIST CSF 2.0. You’ll have to bear with me because the FISMA report is not as detailed as I’d need it to be (which is understandable given security concerns) to give an accurate representation. However I will get it as close as I can!
