My process in determining the policy and practice maturity has been lengthy, but I take pride in it being thorough. I first would read through the FISMA Report. There were 8 points of contention that the Office of Inspector General (OIG) and their contractor Clifton Larson Allen LLP (CLG) found with the VA’s current security posture:
- Agency-Wide Security Management Program
- Identity Management and Access Controls
- Configuration Management Controls
- System Development and Change Management Controls
- Contingency Planning
- Incident Response and Monitoring
- Continuous Monitoring
- Contractor Systems Oversight
For each of these deficiencies I would try to match the subject matter as best as I could to one of the NIST CSF’s Subcategories. As I mentioned previously, the FISMA Report is not the most detailed, so I had to take liberties in postulating what the FISMA Report was exactly insinuating.
FISMA Report Translation
Here is where I would simply read through and annotate my FISMA translations directly from the report:

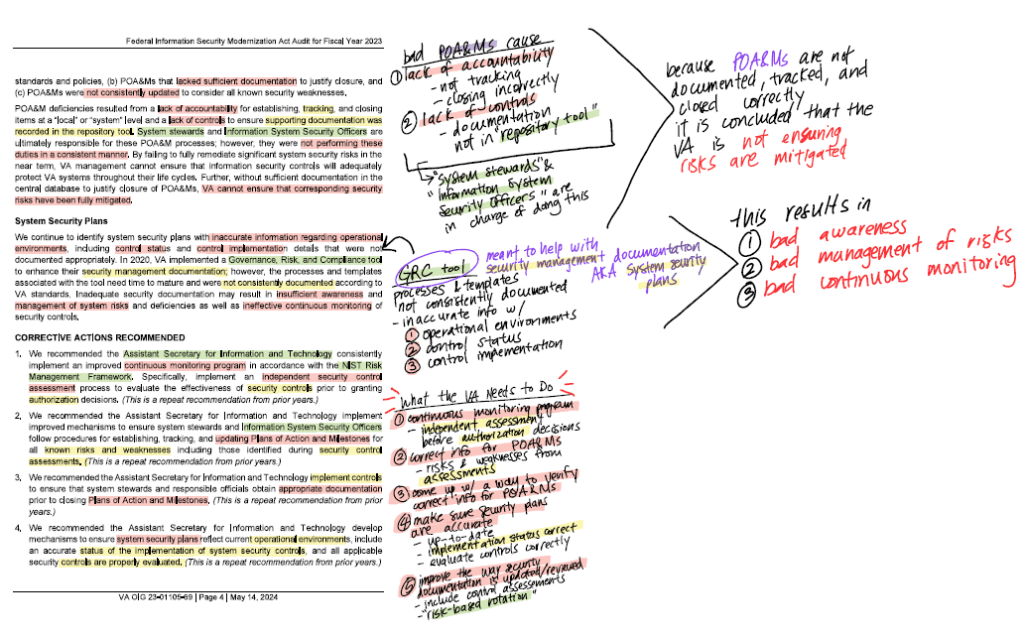


NIST CSF Mapping
Then I would take whatever notes I gathered from the FISMA Report and map it to NIST CSF Subcategories, like I did here:

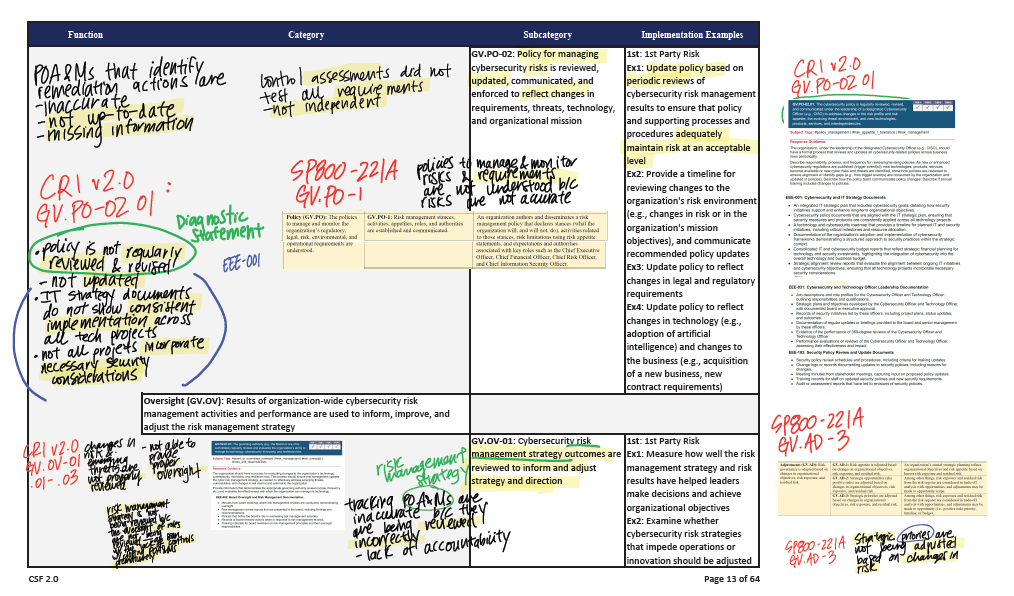

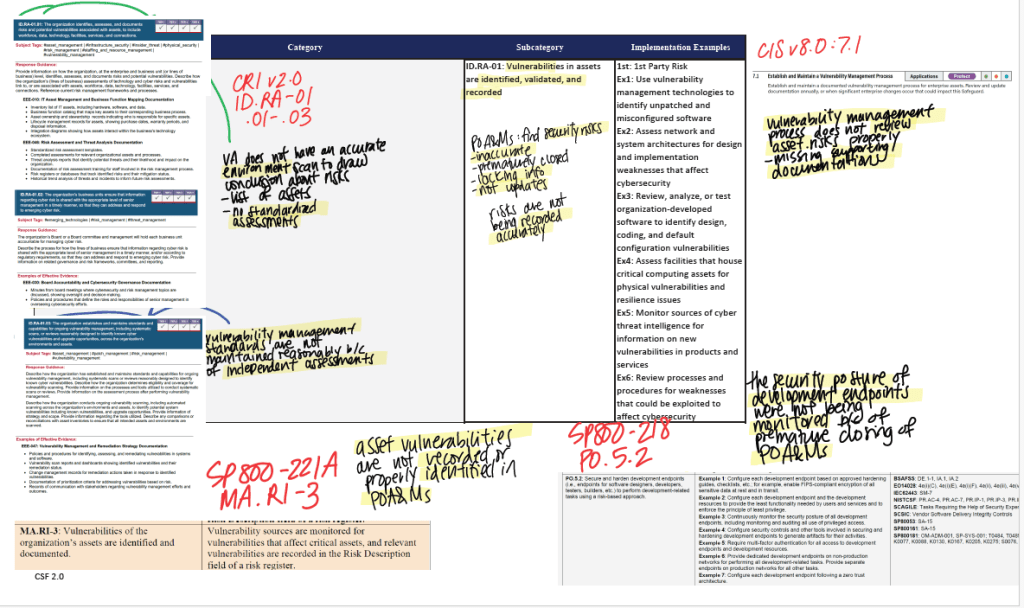
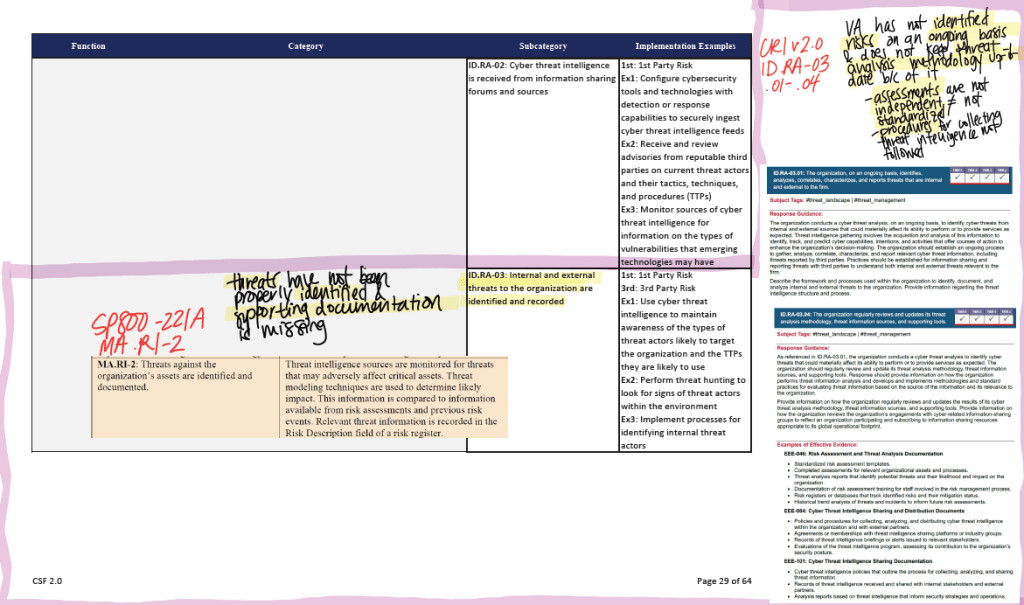
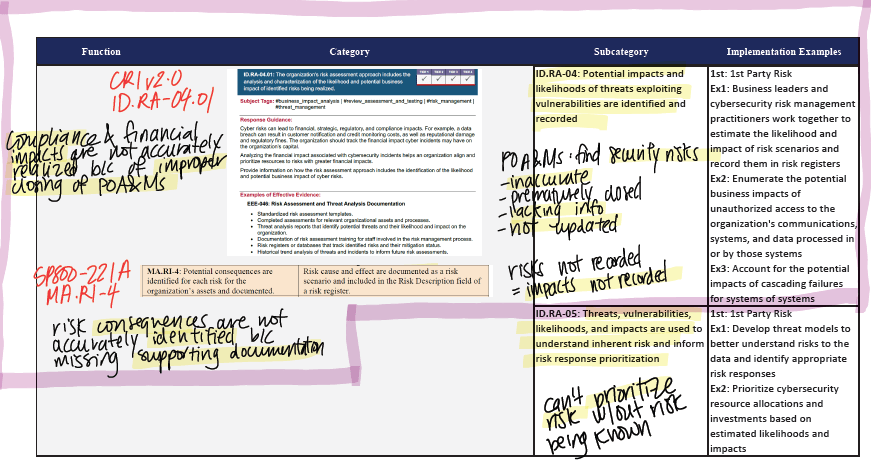
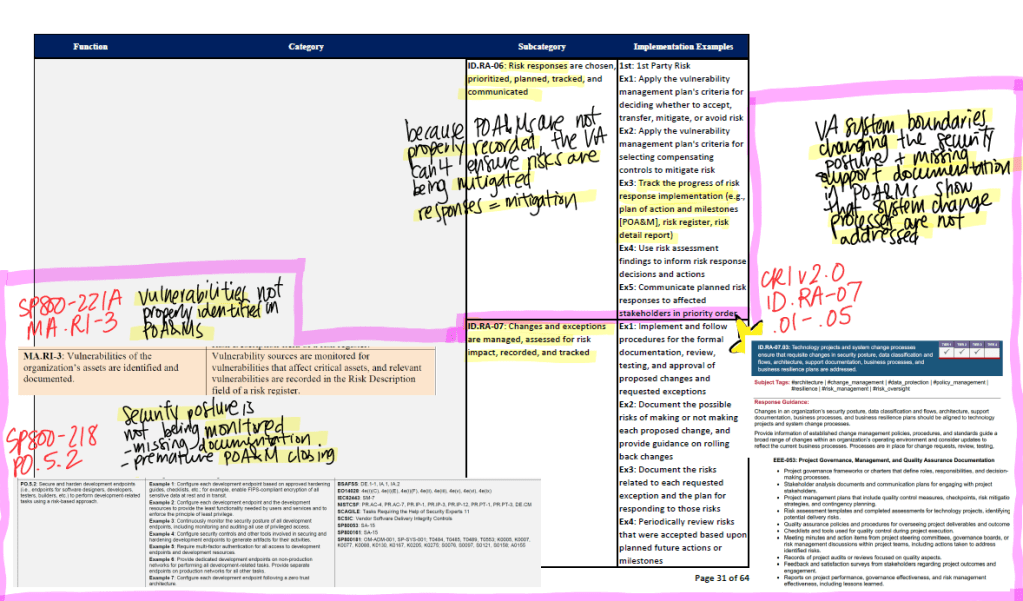
As you can see here I made sure to pull from the documentation also listed in the Subcategory’s Informative Refereces. This would include any SP 800, CRI, and CIS Control documentation. Even though this was quite exhuasting (and it is not lost upon me that AI could do this in less than 2 seconds), I found this really helpful in not only familiarizing myself with the material, but also in seeing the differences between each regulatory lens. While they are all overlapping in the same conceptual matter, they all brought something slightly unique to the table.
For example, CRI v2.0 would show examples of operational scenarios to show actionable steps a company could take. The CIS Controls would list specific safeguards and implementation groups categorized by maturity and resource level. And the SP 800 would provide detailed guidance and technical controls rooted in federal cybersecurity policy and risk management frameworks.
NIST CSF Grading
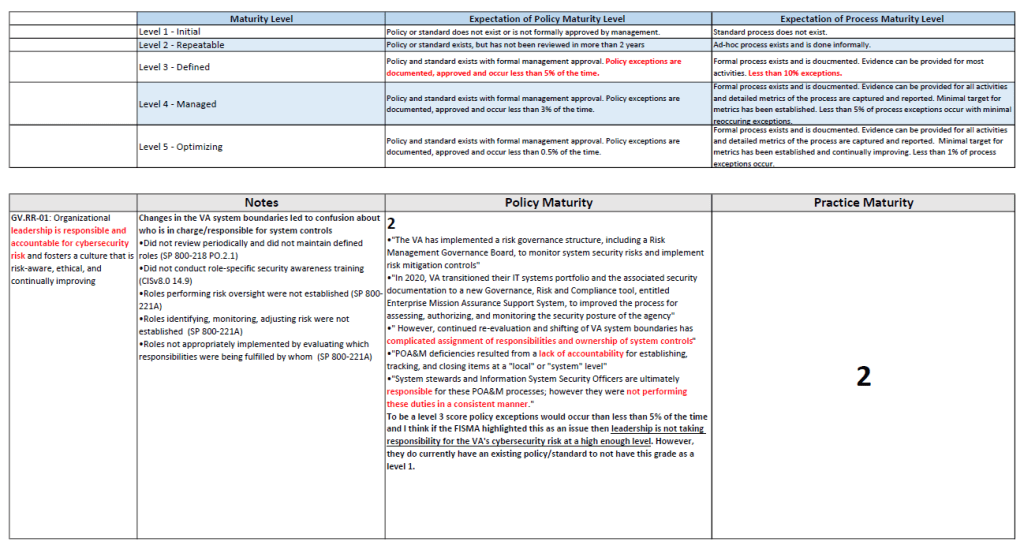
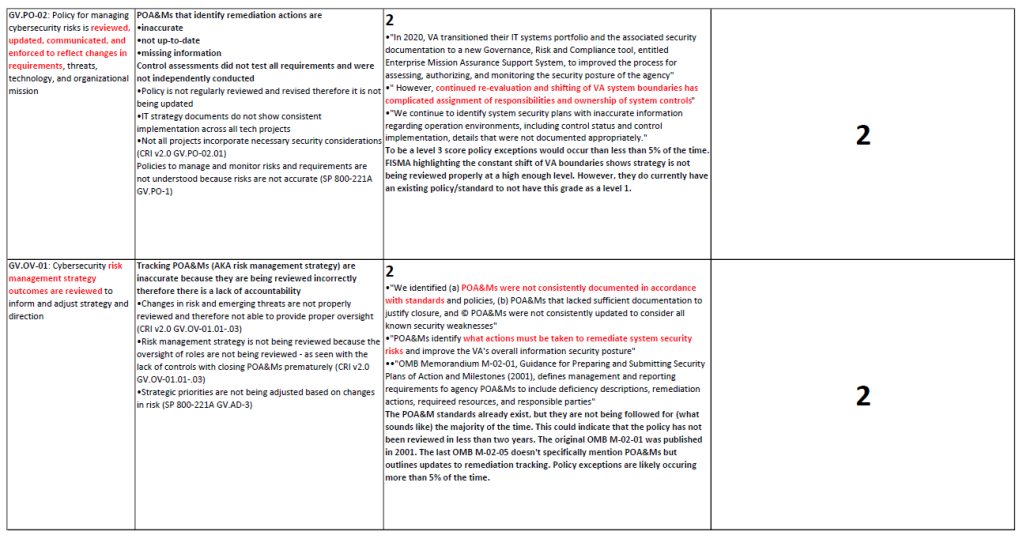
I found that grading based on the FISMA Report was often repetitive, as the Policy and Practice Grades were derived from the same source (the FISMA Report). Additionally, the rigid percentage-based threshold for exceptions left little room for ambiguity. Therefore you’ll see here all the grades under the Security Management Subcategories all received a 2.
I’m attaching these here so you can see the explanations as to why they all received a 2 (also to prove I did not lazily slap on a grade and call it a day). The reasoning as to why the Practice Grade received the same score as the Policy is elaborated in detail under the Policy Grade.
Without further ado:

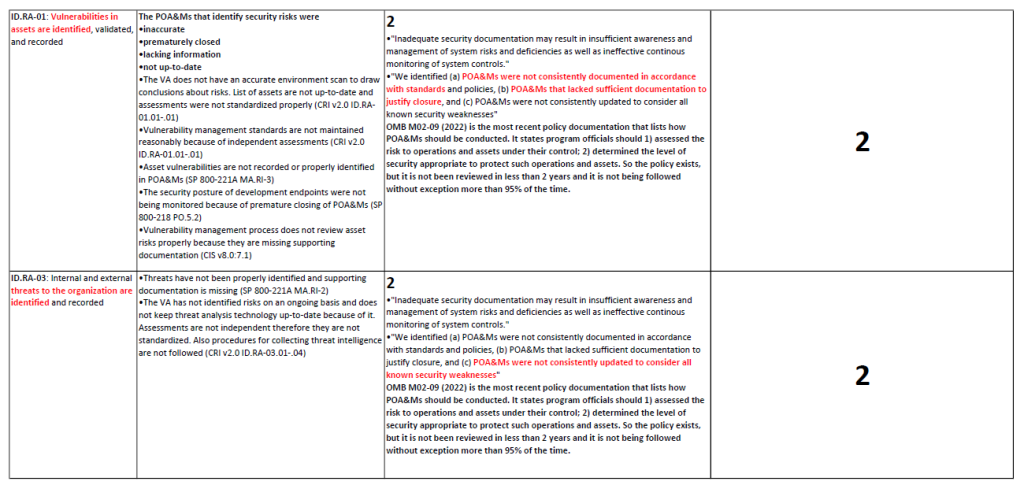
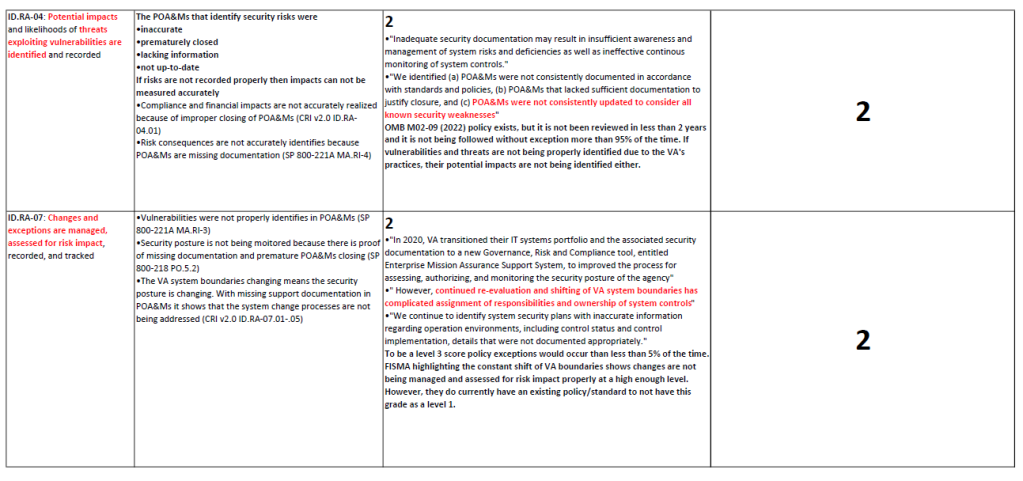
One section down. Seven more to go.
Talk soon…
